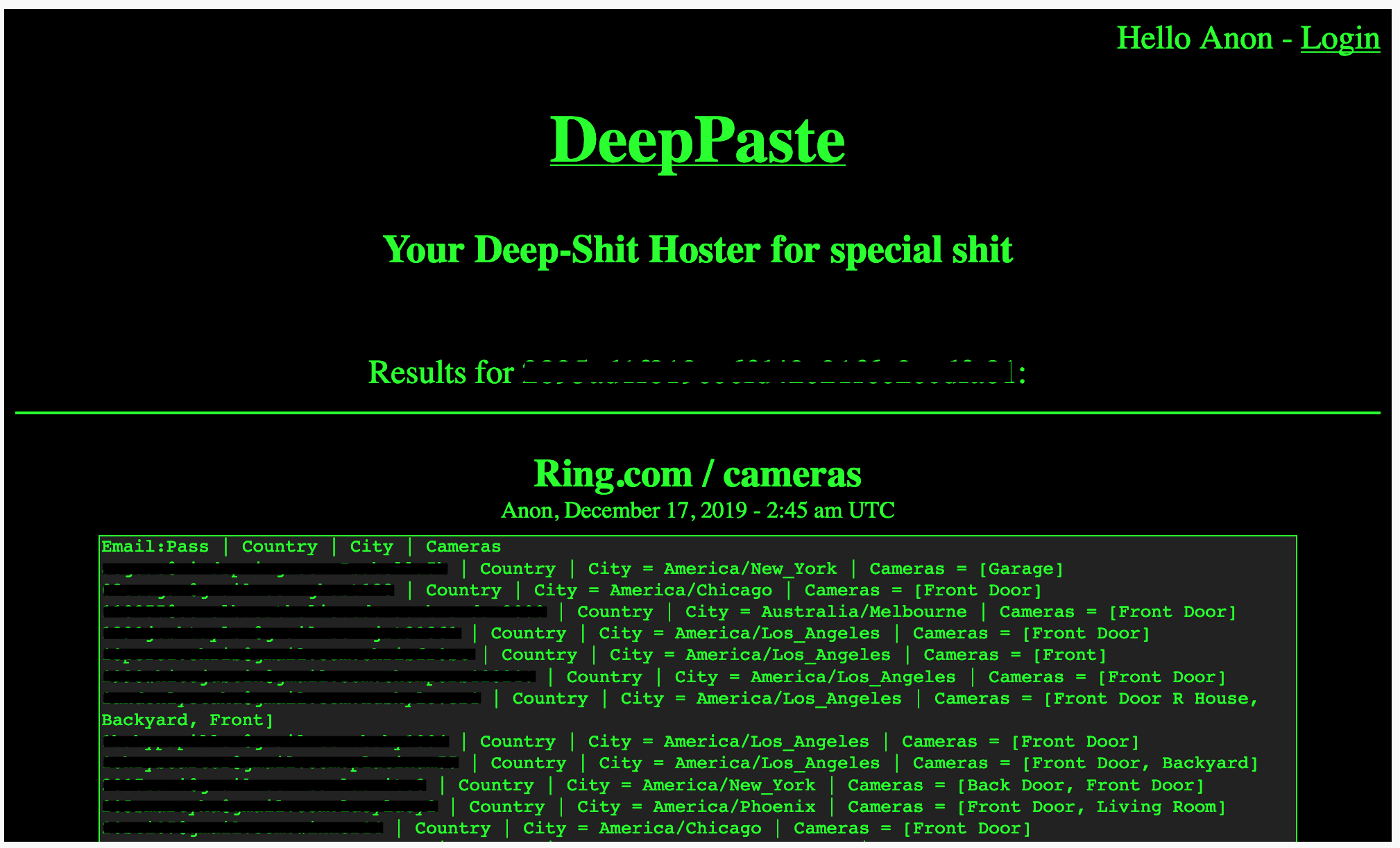
INSUBCONTINENT EXCLUSIVE:
A security researcher has found on the dark web 1,562 unique email addresses and passwords associated with Ring doorbell passwords.
The
list of passwords was uploaded on Tuesday to an anonymous dark web text-sharing site, commonly used to share stolen passwords and illicit
A security researcher found the cache of email addresses and passwords, which can be used to log in to and access the cameras, as well as
their time zone and the doorbell location, such as &driveway& or &front door.&
The researcher reported the findings to Amazon — which owns
the Ring brand — but Amazon asked that the researcher not discuss their findings publicly.
At the time of writing, the dark web listing is
still accessible.
It the second reported leak of Ring credentials today
Earlier on Thursday, BuzzFeed News reported that a similar cache of data on more than 3,600 Ring doorbells was posted online
The data appears to be a similar-looking data set to that which BuzzFeed obtained
Anyone with a working email address and password can log into a Ring account and obtain the Ring customer address, phone number and some
The credentials also give the user access to the Ring devices in that home, including access to historical video data if the setting is
enabled.
It not known how the data was exposed.
The dark web listing (Image: TechCrunch)
TechCrunch contacted a dozen individuals whose
information was found on the dark web listing
We provided each person with their password
Of those who responded, all confirmed that it was their password.
On our advice, all changed their passwords, and some enabled two-factor
authentication on their accounts.
Nearly all of the passwords we reviewed were relatively simple and potentially easy to guess
It possible that the passwords were obtained by password spraying, a technique hackers use to guess passwords, or credential stuffing, where
hackers take existing sets of exposed or breached usernames and passwords matched against different websites to access accounts.
Ring
spokesperson Yassi Shahmiri did not respond to a request for comment prior to publication but in an email after we posted denied a data
breach.
&We&ve notified customers whose accounts we have identified as exposed and have reset their passwords
In addition, we are continuing to monitor for and block potentially unauthorized login attempts into Ring accounts,& the spokesperson
said.
However, of those we spoke to none had been contacted by Ring — contrary to the company claim.
It the latest security lapse
involving Ring security cameras in the past week
News reports emerged last week of how hackers were breaking into Ring cameras around the U.S
Some crime forums are sharing tools to break into Ring accounts
Then earlier this week, Motherboard confirmed that Ring cameras have shoddy security measures — such as not telling users when other
people log in, when the cameras are being actively watched and by using a weak form of two-factor authentication
Ring put much of the blame on the users for not using &best practices.& But others panned the response for failing to put in &basic security
measures& to protect users.
Ring has also come under fire by lawmakers for its close relationship with law enforcement agencies around the
U.S.
It not known how many sets of exposed Ring account credentials are floating around the dark web
Users should protect their accounts with strong, unique passwords and enable two-factor authentication.
Updated with comment from
Ring.
Many smart home device makers still won&t say if they give your data to the government