INSUBCONTINENT EXCLUSIVE:
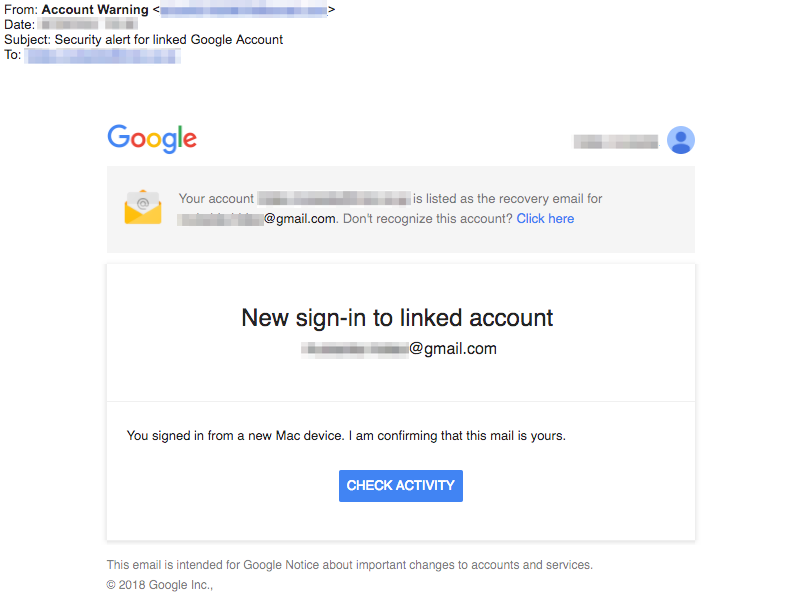
Enlarge / This phishing message used Google's link-shortening service, allowing researchers to learned details about potential targets
(credit: ProtectWise)
Researchers said Chinese intelligence officers are behind almost a decade's worth of network intrusions that use
advanced malware to penetrate software and gaming companies in the US, Europe, Russia, and elsewhere
The hackers have struck as recently as March in a campaign that used phishing emails in an attempt to access corporate-sensitive Office 365
In the process, they made serious operational security errors that revealed key information about their targets and possible
location.
Researchers from various security organizations have used a variety of names to assign responsibility for the hacks, including
LEAD, BARIUM, Wicked Panda, GREF, PassCV, Axiom, and Winnti
In many cases, the researchers assumed the groups were distinct and unaffiliated
According to a 49-page report published Thursday, all of the attacks are the work of Chinese government's intelligence apparatus, which the
report's authors dub the Winnti Umbrella
Researchers from 401TRG, the threat research and analysis team at security company ProtectWise, based the attribution on common network
infrastructure, tactics, techniques, and procedures used in the attacks as well as operational security mistakes that revealed the possible
location of individual members.
A decade of hacks
Attacks associated with Winnti Umbrella have been active since at least 2009 and possibly
In 2013, antivirus company Kaspersky Lab reported that hackers using computers with Chinese and Korean language configurations used a
backdoor dubbed Winnti to infect more than 30 online video game companies over the previous four years
The attackers used their unauthorized access to obtain digital certificates that were later exploited to sign malware used in campaigns
targeting other industries and political activists.
Read 14 remaining paragraphs | Comments