Technology
Lithium
Klout, a service that tracks how much social media attention its users draw and rates their expertise based on the content of their posts, will be switched off on May 25—an announcement that has ironically had Klout trending on Twitter today.
The service, which launched in 2008, also offered an application-programming interface that allowed businesses to collect analytics data about their audiences. Klout also offered "perks" to individuals based on their scores and demographics.
Read 9 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Klout is out-- social media mojo-ranking service to shutter
Write comment (91 Comments)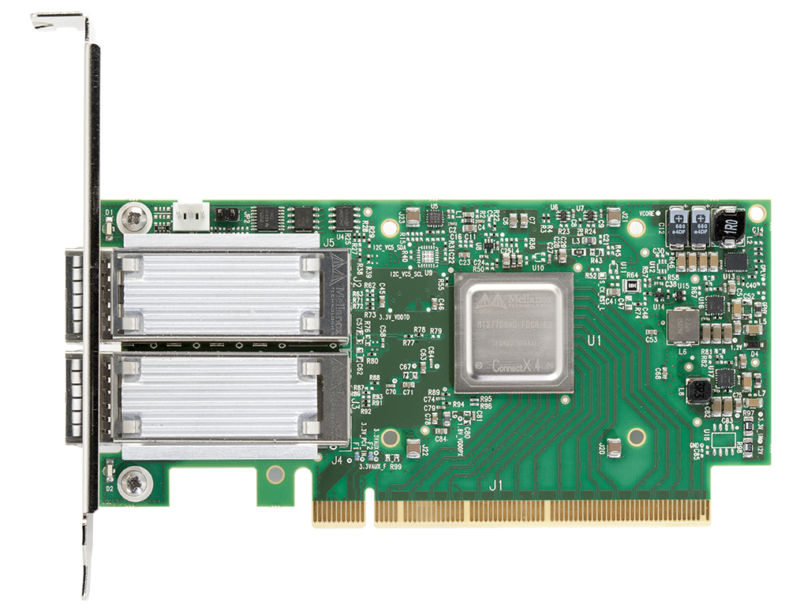
Enlarge / Researchers used a network card like this one in a Rowhammer attack that needed only packets sent over a LAN to work. (credit: Mellanox)
For the first time, researchers have exploited the Rowhammer memory-chip weakness using nothing more than network packets sent over a local area network. The advance is likely to further lower the bar for triggering bit flips that change critical pieces of data stored on vulnerable computers and servers.
Until now, Rowhammer exploits had to execute code on targeted machines. That hurdle required attackers to either sneak the unprivileged code onto the machines or lure end users to a website that hosted malicious JavaScript. In a paper published Thursday, researchers at the Vrije Universiteit Amsterdam and the University of Cyprus showed that standard packets sent over networks used by many cloud services, universities, and others were sufficient. The secret to the new technique: increasingly fast network speeds that allow hackers to send specially designed packets in rapid succession.
"Thus far, Rowhammer has been commonly perceived as a dangerous hardware bug that allows attackers capable of executing code on a machine to escalate their privileges," the researchers wrote. "In this paper, we have shown that Rowhammer is much more dangerous and also allows for remote attacks in practical settings. We show that even at relatively modest network speeds of 10Gbps, it is possible to flip bits in a victim machine from across the network."
Read 9 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Packets over a LAN are all it takes to trigger serious Rowhammer bit flips
Write comment (92 Comments)
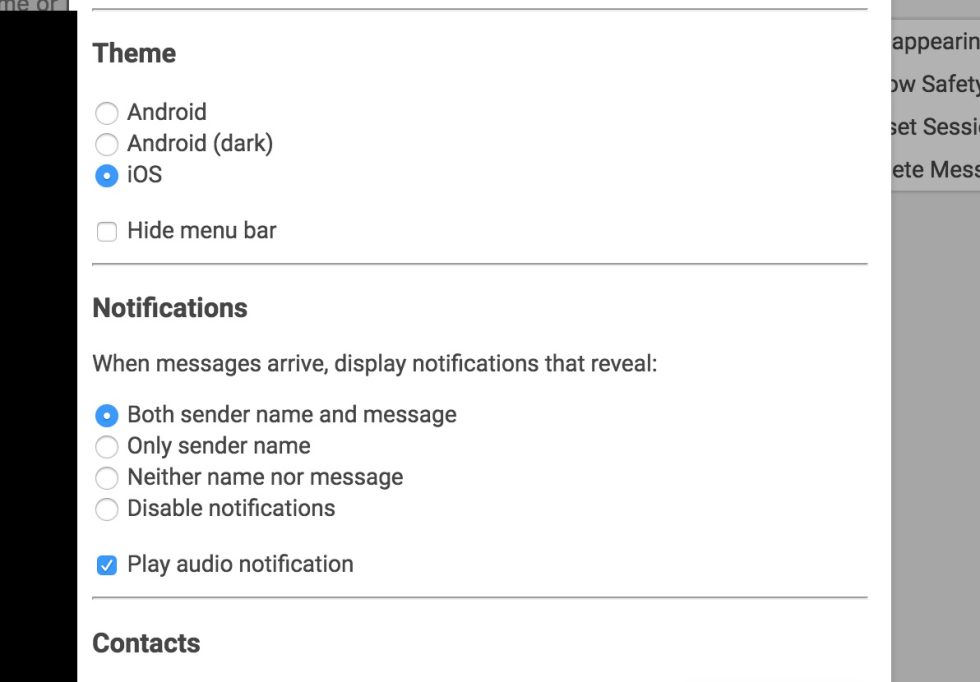
Enlarge / You may want to nicely ask your friends who use Signal on the Mac desktop to change their notification settings. (credit: Signal)
Signal, the privacy-focused voice and text-messaging application, offers an attractive bit of operational security: ephemeral text messages that "self-delete" after a predetermined amount of time. There is just one small problem, however, with that feature on the Mac desktop version of the application, as information security consultant Alec Muffett discovered: if you send a self-deleting message to someone using the macOS application, the message lives on in macOS' Notifications history.
#HEADSUP: #Security Issue in #Signal. If you are using the @signalapp desktop app for Mac, check your notifications bar; messages get copied there and they seem to persist — even if they are "disappearing" messages which have been deleted/expunged from the app. pic.twitter.com/CVVi7rfLoY
— Alec Muffett (@AlecMuffett) May 8, 2018
Ars reproduced the problem, which Patrick Wardle of Objective See conducted a particularly deep dive on—revealing that the problem is, in part, a bug in the way Signal handles calls to the macOS notification system and, in part, is just how macOS notifications work.
Read 3 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Signal’s “disappearing messages” live on in macOS notifications
Write comment (92 Comments)
Canonical recently released Ubuntu 18.04, the company's latest iteration of its popular Linux distribution, nicknamed Bionic Beaver. Ubuntu 18.04 is a Long Term Support (LTS) release and will receive updates and support from Canonical until April 2023. But more notably
Unity is gone. GNOME is back. And Ubuntu has never been better.
Read 44 remaining paragraphs | Comments
- Details
- Category: Technology

Enlarge (credit: Getty Images)
On Wednesday, the California Energy Commission approved a set of standards that will require most new homes built in the state after 2020 to include solar panels on their roofs.
The standards(PDF) apply only to single-family homes and certain low-rise condos, townhomes, and apartments. Exceptions are made for homes with roofs that would receive excessive shade during the daytime or homes with roofs too small to benefit from a few solar panels.
The standards also include some smaller efficiency requirements for non-residential buildings. The state expects that, on the whole, the new requirements will help state residents save money. Overall, California expects the new residential and non-residential standards to cost the state economy $2.17 billion, while generating an energy bill savings of $3.87 billion, for a net savings of $1.7 billion.
Read 4 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: California approves measure to require solar on new homes after 2020
Write comment (98 Comments)
Enlarge / Georgia Governor Nathan Deal, with wife Sandra Deal, receives the Infinity Gauntlet from Mitch Bell on April 26, 2018 in Atlanta, Georgia. It is not known if he used the gauntlet to apply the veto stamp to Senate Bill 315, which would have criminalized some security research while allowing companies to "hack back." (credit: Paras Griffin/Getty Images)
A bill passed by Georgia's legislature that would have criminalized unauthorized access of computer systems and allowed companies to "hack back" in defense against breaches was vetoed on May 8 by Georgia Governor Nathan Deal. The veto came after many weeks of opposition from information security firms and professionals, as well as major technology companies—including Google and Microsoft executives, who expressed concern that the bill would actually make it more difficult to secure computer systems.
Given that Georgia is the home of Fort Gordon, an Army base that serves as home to units of the Army's Cyber Command and to parts of the National Security Agency, and that Georgia has become home to an increasing number of cybersecurity firms as a result both of the Army/NSA presence and research at Georgia's universities, Deal realized after feedback from the industry that the bill could have resulted in inadvertent damage.
But Deal's reasoning wasn't necessarily what individuals in the information security research community would have hoped for. And there's still a chance that another bill—one more acceptable to technology giants but still criminalizing some aspects of information security research—could emerge in the next legislative session and win Deal's approval.
Read 7 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Georgia guv vetoes cyber expense that would criminalize unauthorized access
Write comment (92 Comments)Page 5433 of 5614

 12
12