Technology

Enlarge / Encrypting DNS traffic between your device and a "privacy-focused" provider can keep someone from spying on where your browser is pointed or using DNS attacks to send you somewhere else. (credit: Westend61 / Getty Images)
In this op-ed, a group of noted security researchers takes aim at Ray Ozzie's plan to grant law enforcement access to encrypted devices—and to do so securely. The views here do not necessarily represent those of Ars Technica.
In the debate over law enforcement access to encrypted devices, technical details matter. The rhetoric has been stark and, dismayingly often, divorced from technical reality. For example, two years ago we were told that only Apple could write software to open the phone of the San Bernardino terrorist; the technical reality turned out to be that an FBI contractor was able to do so. More recently, the rhetoric has been about the thousands of phones that are part of criminal investigations and that law enforcement cannot unlock. Todayreality is that Grayshift will sell law enforcement a $15,000 tool that opens 300 locked phones or online access for $30,000 to open as many phones as law enforcement has warrants for.
Into this conflict comes a Wired article suggesting that Ray Ozzie, the inventor of Lotus Notes and a former VP at Microsoft, has a solution to the exceptional access problem (the ability for law enforcement with a warrant to open a locked device). The article is yet another example of the wide gap between wishful rhetoric and technical reality.
Read 9 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Op-ed: Ray Ozzie’s crypto proposal—a dose of technical reality
Write comment (96 Comments)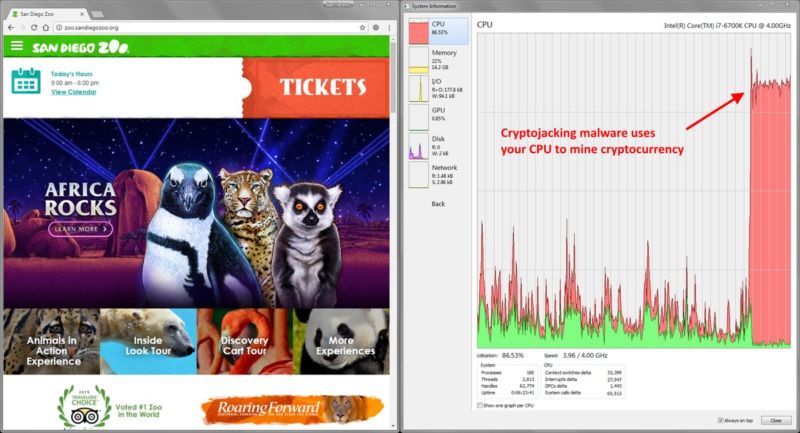
Enlarge / Not the experience you wanted from the San Diego Zoo website. (credit: Troy Mursch)
A mass hacking campaign that targets a critical vulnerability in the Drupal content management system has converted more than 400 government, corporate, and university websites into cryptocurrency mining platforms that surreptitiously drain visitors' computers of electricity and computing resources, a security researcher said Monday.
Sites that were hacked included those belonging to computer maker Lenovo, the University of California at Los Angeles, the US National Labor Relations Board, the Arizona Board of Behavioral Health Examiners, and the city of Marion, Ohio, Troy Mursch, an independent security researcher, told Ars on Monday. The Social Security Institute of the State of Mexico and Municipalities, the Turkish Revenue Administration, and Peru's Project Improvement of Higher Education Quality were also affected. The US had the largest concentration of hacked sites, with at least 123, followed by France, Canada, Germany, and the Russian Federation, with 26, 19, 18 and 17, respectively.
The sites all ran the same piece of JavaScript hosted on vuuwd.com. The highly obfuscated code caused visitors' computers to dedicate 80 percent of their CPU resources to mining the digital coin known as Monero with no notice or permission. The attacker behind the campaign took control of the sites by exploiting a Drupal vulnerability that makes code-execution attacks so easy and reliable it was dubbed "Drupalgeddon2." Although Drupal maintainers patched the critical flaw in March, many vulnerable sites have been slow to install the fix. The lapse touched off an arms race among malicious hackers three weeks ago.
Read 5 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Hundreds of big-name sites hacked, converted into drive-by currency miners
Write comment (93 Comments)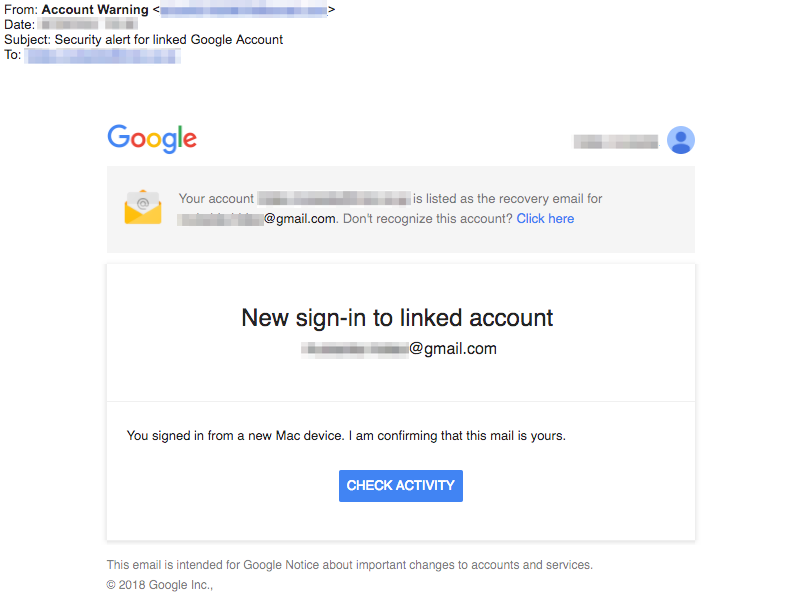
Enlarge / This phishing message used Google's link-shortening service, allowing researchers to learned details about potential targets. (credit: ProtectWise)
Researchers said Chinese intelligence officers are behind almost a decade's worth of network intrusions that use advanced malware to penetrate software and gaming companies in the US, Europe, Russia, and elsewhere. The hackers have struck as recently as March in a campaign that used phishing emails in an attempt to access corporate-sensitive Office 365 and Gmail accounts. In the process, they made serious operational security errors that revealed key information about their targets and possible location.
Researchers from various security organizations have used a variety of names to assign responsibility for the hacks, including LEAD, BARIUM, Wicked Panda, GREF, PassCV, Axiom, and Winnti. In many cases, the researchers assumed the groups were distinct and unaffiliated. According to a 49-page report published Thursday, all of the attacks are the work of Chinese government's intelligence apparatus, which the report's authors dub the Winnti Umbrella. Researchers from 401TRG, the threat research and analysis team at security company ProtectWise, based the attribution on common network infrastructure, tactics, techniques, and procedures used in the attacks as well as operational security mistakes that revealed the possible location of individual members.
A decade of hacks
Attacks associated with Winnti Umbrella have been active since at least 2009 and possibly date back to 2007. In 2013, antivirus company Kaspersky Lab reported that hackers using computers with Chinese and Korean language configurations used a backdoor dubbed Winnti to infect more than 30 online video game companies over the previous four years. The attackers used their unauthorized access to obtain digital certificates that were later exploited to sign malware used in campaigns targeting other industries and political activists.
Read 14 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: Report: Chinese government is behind a decade of hacks on software companies
Write comment (95 Comments)
Enlarge / Cloudflare's DNS service uses the 1.1.1.1 address. (credit: Cloudflare)
AT-T has been blocking the new Cloudflare DNS service, but AT-T says the blocking was unintentional and that it will fix the problem soon.
The blocking is affecting AT-T home Internet customers who use an AT-T gateway. Cloudflare unveiled its DNS service on April 1, and users in DSLReports forum threads almost immediately started complaining that they couldn't access it. One thread began on April 1, within hours of Cloudflare's announcement.
"I am now unable to reach 1.1.1.1 and 1.0.0.1, which is unfortunate because those are the DNS servers I use," one user wrote.
Read 21 remaining paragraphs | Comments
- Details
- Category: Technology
Read more: AT T explains why it blocked Cloudflare DNS: It was just an accident
Write comment (92 Comments)
- Details
- Category: Technology
Read more: Hitting the road Leave your laptop at home
Write comment (93 Comments)
Microsoft's new move to put PR groups inside its operating divisions is paying off. We're now seeing the worst news shuffled out the door on Friday nights. This week's instance addresses a years-long fight by afflicted Surface Pro 4 users to get Microsoft to admit it has a problem, and to provide redress.
Flickergate, you may recall, involves the propensity of some Surface Pro 4 machines to flicker violently. You can see the shake — dating to March 6, 2016, mind you — in a YouTube video posted by Dmitriy1986.
I've written about the flicker, and Microsoft's abhorrent treatment of its customers, on April 4, 2017, Aug. 1, 2017, Nov. 13, 2017, Feb. 7, 2018, and Mar. 21, 2018.
- Details
- Category: Technology
Read more: Microsoft finally stops screwing Surface Pro 4 owners with flickergate
Write comment (95 Comments)Page 5435 of 5614

 13
13